Ok, so I thought I was grasping the whole Access-list thing pretty well until I got to the practice tests concerning inbound/outbound traffic.
When this is used... how should I interpret incoming/outgoing traffic? IE:
inbound as in coming in FROM an outside source, or Inbound as in already inside the subnet of the router?
I hope you understand what I am talking about. (although I am already confusing myself)
This is driving me crazy.
Here is a proposed question that i though I got right but ended up being wrong about.
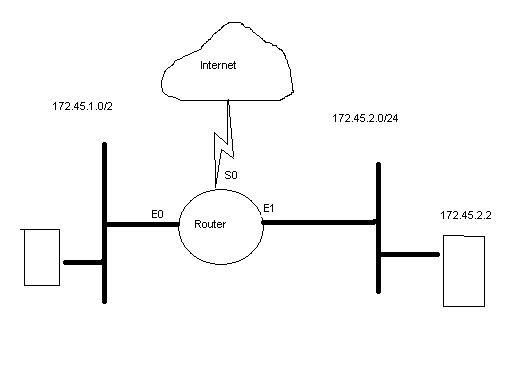
Some guy has two subnets, 172.45.1.0 and 172.45.2.0. You want to protect the 172.45.2.0 subnet from all traffic except for the 172.45.1.0 network; But you don't want anyone to telnet into 172.45.2.2. You currently do not have any filters on.
So you go ahead and insert the following lists.
access-list 102 deny tcp 172.45.1.0 0.0.255.255 host 172.45.2.2 eq 23
access-list 102 permit ip 172.45.1.0 0.0.255.255 172.45.2.0 0.0.0.255
Where should you apply the 102 filter?
1. Outbound side of E1
2. Inbound side of E0
3. Inbound side of S0
4. Inbound side of E1
5. Outbound side of E0
Now, since it asks me to protect the subnet I chose the Inbound side of E1... trying to stop inbound traffic to the subnet.
Now they say the answer is the Outbound side of E1... (Which makes me think that they are trying to block all traffic leaving the 172.45.2.0 subnet.
Have I just lost it?
Thanks for reading all the way through! (if you did ha ha)